Microsoft Entra ID
Overview
Microsoft Entra ID (formerly Azure Active Directory) for IPscape gives Administrators the ability to simplify access and manage Agents or Users accessing the Workspace, Agent Toolbar, or the CTI Adaptor.
Microsoft Entra ID Integration with IPscape can be utilised with the following features and the configuration for each, once an Entra ID Application is created, is listed:
Single Sign-On (SSO):
Redirect URI required
Exchange Online for Email Channels:
Client Secret required
Redirect URI required
Agent Toolbar Contact Directory for Manual Calls, Transfers and Email:
Client Secret required
API Permissions (See Additional Notes, #1)
A single IPscape Entra ID application can be configured in the portal of each of the above
1. Adding a Microsoft Entra ID Application for IPscape
Global Administrator permissions for the Entra ID user configuring the application is required to complete the following sections.
To create the registration of IPscape in Azure Active Directory:
Sign in to the Entra ID portal
If there is access to multiple tenants, use the Directories + subscriptions filter in the top menu to switch to the tenant which will be registered to the IPscape workspace.
Search for and select Azure Active Directory.
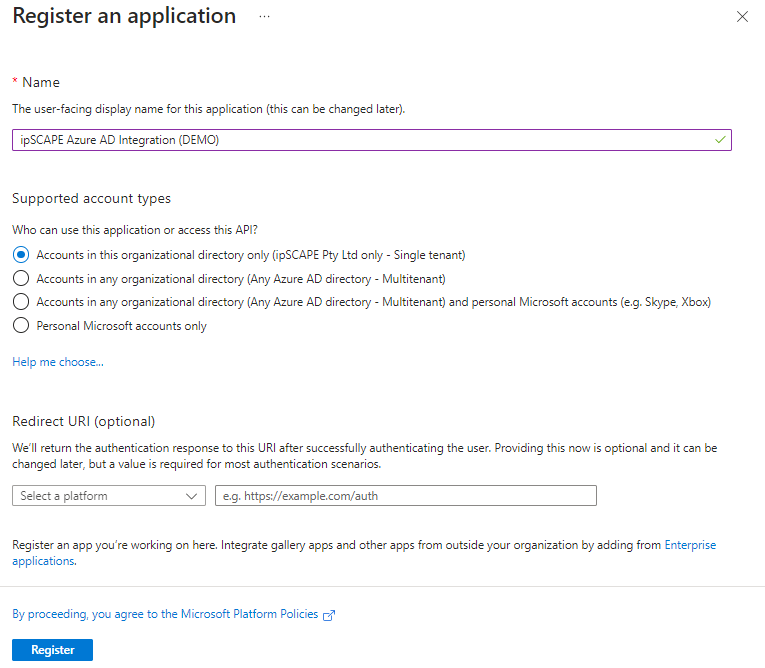
Under Manage, select App registrations > New registration.
Enter a display Name, for example “IPscape Azure AD Integration (DEMO)”
Specify who can use the application, this may also be called its “Sign-in audience”
Leave Redirect URI (optional) blank; this will be configured in the next section
Select Register to complete the initial app registration
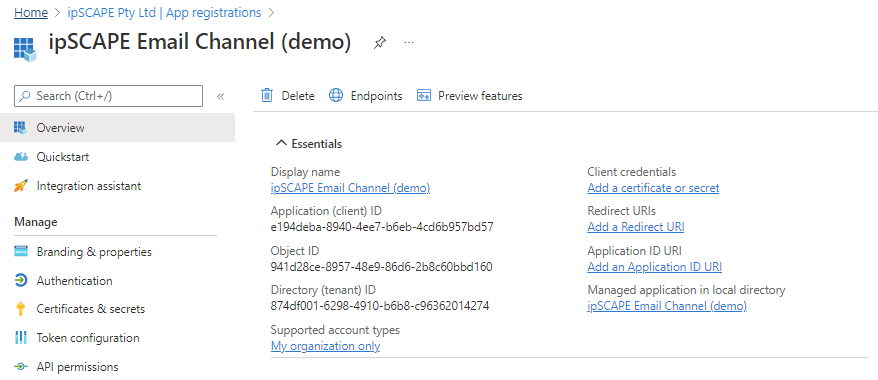
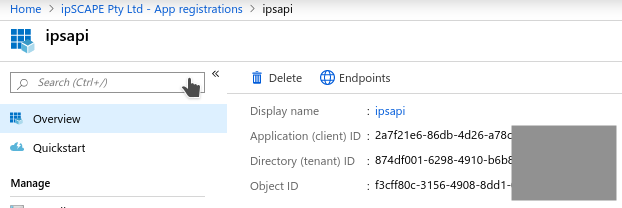
When registration finishes, the Azure portal displays the IPscape app registration Overview pane showing the Application (client) ID and Directory (tenant) ID which are required for the following:
Agent Toolbar Contact Directory Workspace configuration for Manual Calls, Transfers and Email
2. Add a Redirect URI to the Entra ID IPscape Application
A redirect URI is the location where the Microsoft identity platform redirects a user's client and sends security tokens after authentication. A redirect URI can be added or modified by configuring the platform settings.
Redirect URI is required for the configuration of Entra ID in IPscape for:
Single Sign-On (SSO)
Exchange Online for Email Channels
To configure application settings registered in the previous section, follow these steps for each of the above:
In the Azure portal, in App registrations, select the IPscape application.
Under Manage, select Authentication.
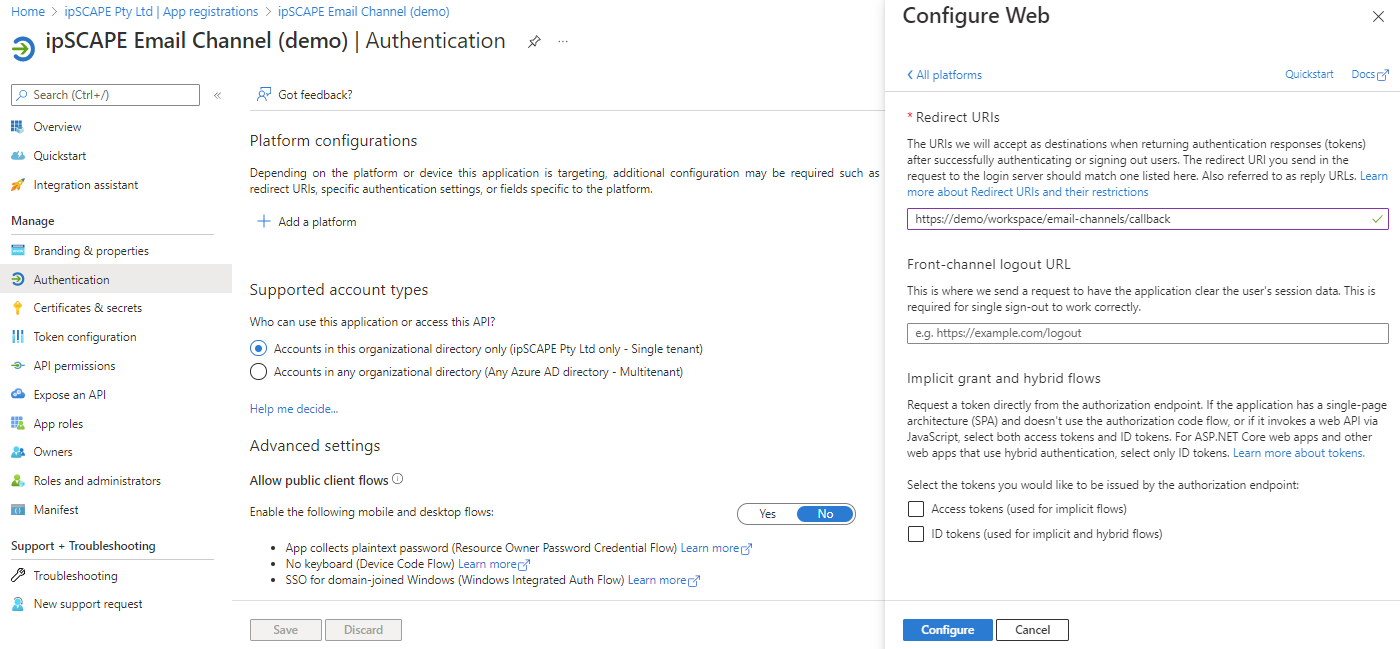
Under Platform configurations, select Add a platform.
Under Configure platforms, select the Web tile to configure the settings:
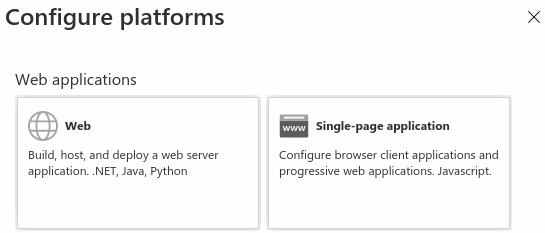
View the relevant sections below for the Redirect URI values to be entered:
Single Sign-On (SSO) Redirect URI Configuration
Enter the Redirect URI and click Configure. The Redirect URIs will be in the following format:
Field | Environment | Value |
Redirect URIs | All Environments CTI Adaptor Users | https://<TENANT_HOSTNAME>/workspace/authorize-sso https://<TENANT_HOSTNAME>/toolbar/login https://<TENANT_HOSTNAME>/cti/login |
Logout URL | All Environments | https://<TENANT_HOSTNAME>/api/latest/user/endthirdpartysession |
ID Tokens | All Environments | Checked |
Click the "Overview" section in Entra, and then configure the IPscape Workspace with the following details to enable the SSO configuration of the credentials into IPscape:
Application (client) ID
Directory (tenant) ID
To see instructions for Workspace configuration please go to Single Sign-on (SSO) Workspace Configuration.
Email Channel Redirect URI Configuration
Enter the Redirect URI and click Configure. The Redirect URI will be in the following format:
https://<your-ipSCAPE-tenant-name>/workspace/email-channels/callback
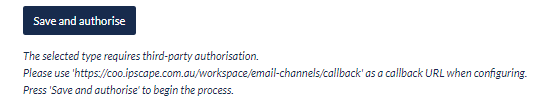
The Redirect URI can also be found in and copied from Workspace > Email Channels when Microsoft Exchange Online is selected as a Type (see below)
3. Client Secret Credentials for Entra ID
Sometimes called an application password, a client secret is a string value that can be used in place of a certificate as identity. The Client Secret is required for the configuration of Entra ID in IPscape for:
Agent Toolbar Contact Directory for Manual Calls, Transfers and Email
Exchange Online for Email Channels
To configure the application Client Secrets:
In the Azure portal, in App registrations, select the application configured in the previous sections.
Select Certificates & secrets > Client secrets > New client secret.
Add a description for the client secret.
Select an expiration for the secret or specify a custom lifetime.
Client secret lifetime is limited to two years (24 months) or less. A custom lifetime can not be longer than 24 months.
It is recommended that an expiration value of less than 12 months is set.
Select Add.
Ensure to record the secret's value as this is required to use in the email channel configuration and Directory configuration in IPscape.
The client secret value will not displayed again after leaving this page.
If lost, a new secret will need to be reconfigured from the steps above.
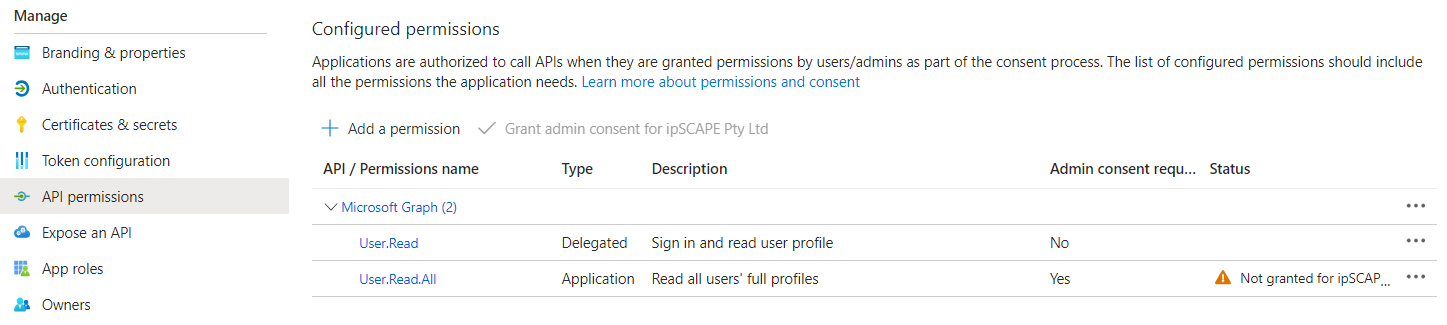
4. Additional Notes
API Permissions for User.Read.All are required to Sync the Directory in the SCAPE Workspace and the User will be presented an error if this is attempted without the permission added to the Azure Application:
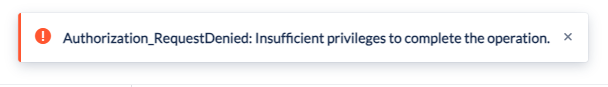
Global Administrator User access is required to grant this permission: